INCIDENT REPORTING MODULE
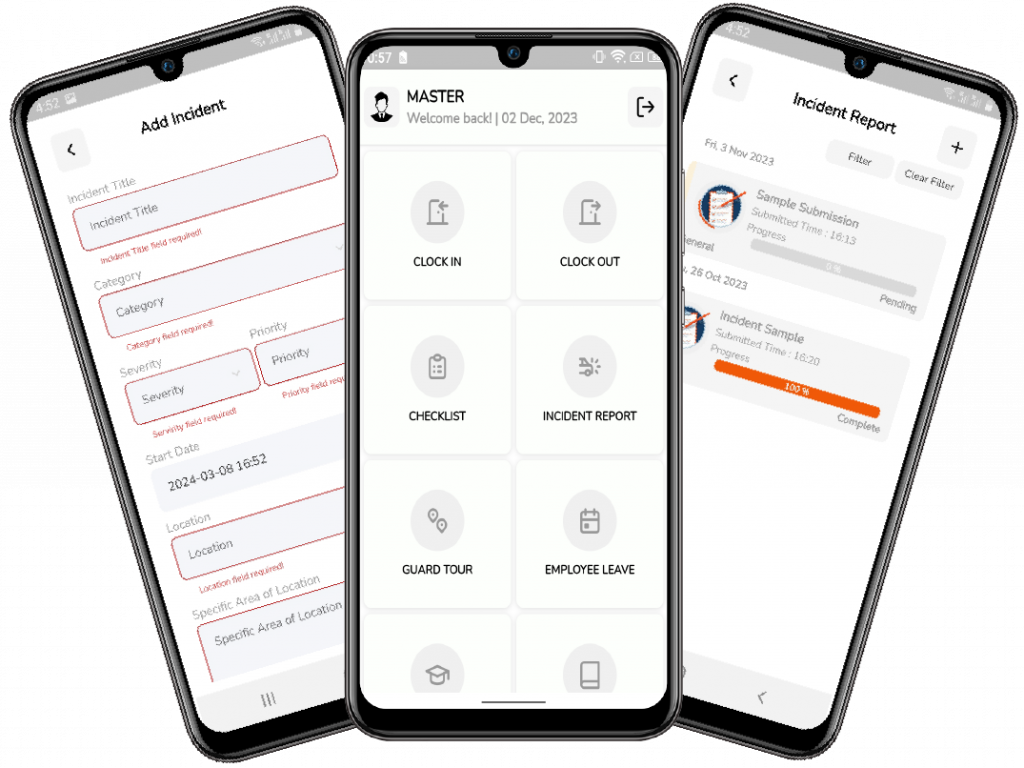
The iSecure360 Incident Reporting module empowers organizations to effectively manage and respond to incidents with precision and efficiency. Equipped with intuitive features, this module enables seamless reporting of security breaches, accidents, and other critical events in real-time. With customizable incident forms and workflows, users can tailor the reporting process to suit specific needs, ensuring accurate and detailed documentation of incidents. Advanced notification capabilities alert relevant stakeholders instantly, facilitating swift response and resolution. Additionally, comprehensive incident logs and analytics provide valuable insights into incident trends and patterns, enabling proactive risk mitigation strategies. From minor incidents to emergencies, the iSecure360 Incident Reporting module ensures thorough incident documentation and streamlined incident management processes, ultimately enhancing security and safety across your organization.
- Electronic incident management system with image capture.
- Keep track of each incident’s status
- Search by multiple conditions ‘When’,’What’,’Who’,’Where’ (Smart Filters)
- Accessible by supervisor and officer anywhere
- Capture all incidents at the site even at places with poor network signal & handle them real-time.
Advantages
- Real-time Reporting: Enable prompt reporting of security breaches and incidents, ensuring timely response and resolution.
- Customizable Forms: Tailor incident reporting forms to specific requirements, capturing detailed and relevant information for comprehensive documentation.
- Enhanced Accountability: Hold individuals accountable for their actions with detailed incident logs and timestamps, promoting transparency and responsibility.
- Streamlined Processes: Simplify incident management workflows, reducing administrative burden and enhancing operational efficiency.
- Compliance Assurance: Ensure compliance with regulatory requirements by maintaining accurate and comprehensive incident records.
- Enhanced Security: Strengthen overall security posture by promptly addressing and resolving reported incidents, minimizing potential threats and vulnerabilities.
- Continuous Improvement: Use incident data and analysis to identify areas for improvement in security protocols and procedures, fostering a culture of continuous enhancement.

